In a time when news of financial data leaks regularly fills the media, safeguarding confidential information is of paramount importance. For CTOs, software developers, and cybersecurity experts in the finance industry, a potent weapon in their security toolkit is code obfuscation.
What is code obfuscation?
Code obfuscation is a security technique that transforms source code or machine code into a version that is difficult for both humans and automated tools to understand, while maintaining its functionality. This process involves altering the structure of the code without changing its output, making it challenging for attackers to reverse engineer or tamper with the software. In the context of financial software, code obfuscation not only protects sensitive algorithms and proprietary trading strategies but also serves as a vital barrier against reverse engineering and malicious intrusions. It plays a crucial role in protecting customer data processing routines.
Let’s explore the reasons why code obfuscation is increasingly essential for organizations and how it can be implemented effectively.
Why code obfuscation matters for business security?
Protection of intellectual property
Financial institutions invest heavily in developing proprietary algorithms and trading strategies. Code obfuscation tools help protect these valuable assets from competitors and malicious parties.
Compliance with regulations
Many financial regulations require robust security measures to protect customer data. Code obfuscation contributes to meeting these compliance requirements by adding an extra layer of security.
Deterrence of reverse engineering
Obfuscated code significantly increases the time and resources required for reverse engineering, deterring potential attackers.
Mitigation of insider threats
Even if an insider gains access to the source code, obfuscation makes it difficult to understand and exploit the code’s logic.
Types of code obfuscation techniques
Lexical and structural obfuscation
- Lexical obfuscation (renaming): involves renaming variables, methods, and classes to meaningless or misleading names.
- Control flow obfuscation: alters the code’s structure by adding redundant code, rearranging the execution order, or inserting complex branching logic.
- Function splitting: breaks down functions into smaller pieces and spreads them across the codebase to obscure logic.
- Inlining: merges multiple functions into one to cloud the logic and purpose of individual functions.
- Opaque predicates: uses conditions that always evaluate to true or false but appear complex, misleading code analysers.
Data and storage obfuscation
- Data obfuscation: transforms data structures and alters how data is stored and accessed. Includes using complex data structures or abstract data types to hide underlying data.
- String encryption: encrypts strings in the code so they are not readable in their original form, requiring decryption at runtime.
- Code insertion (Dead code): adds non-functional code that does not affect the program but makes it harder to read and analyse.
Platform-specific obfuscation
- JavaScript obfuscation: specifically for web applications, this technique makes JavaScript code difficult to read and analyse.
Advanced obfuscation techniques
- Virtualization: transforms code into a form that can be run on a virtual machine, making reverse-engineering more challenging.
- Packing: compresses or encrypts the executable portion of the code, which must be unpacked at runtime, hindering static analysis.
Example of lexical code obfuscation
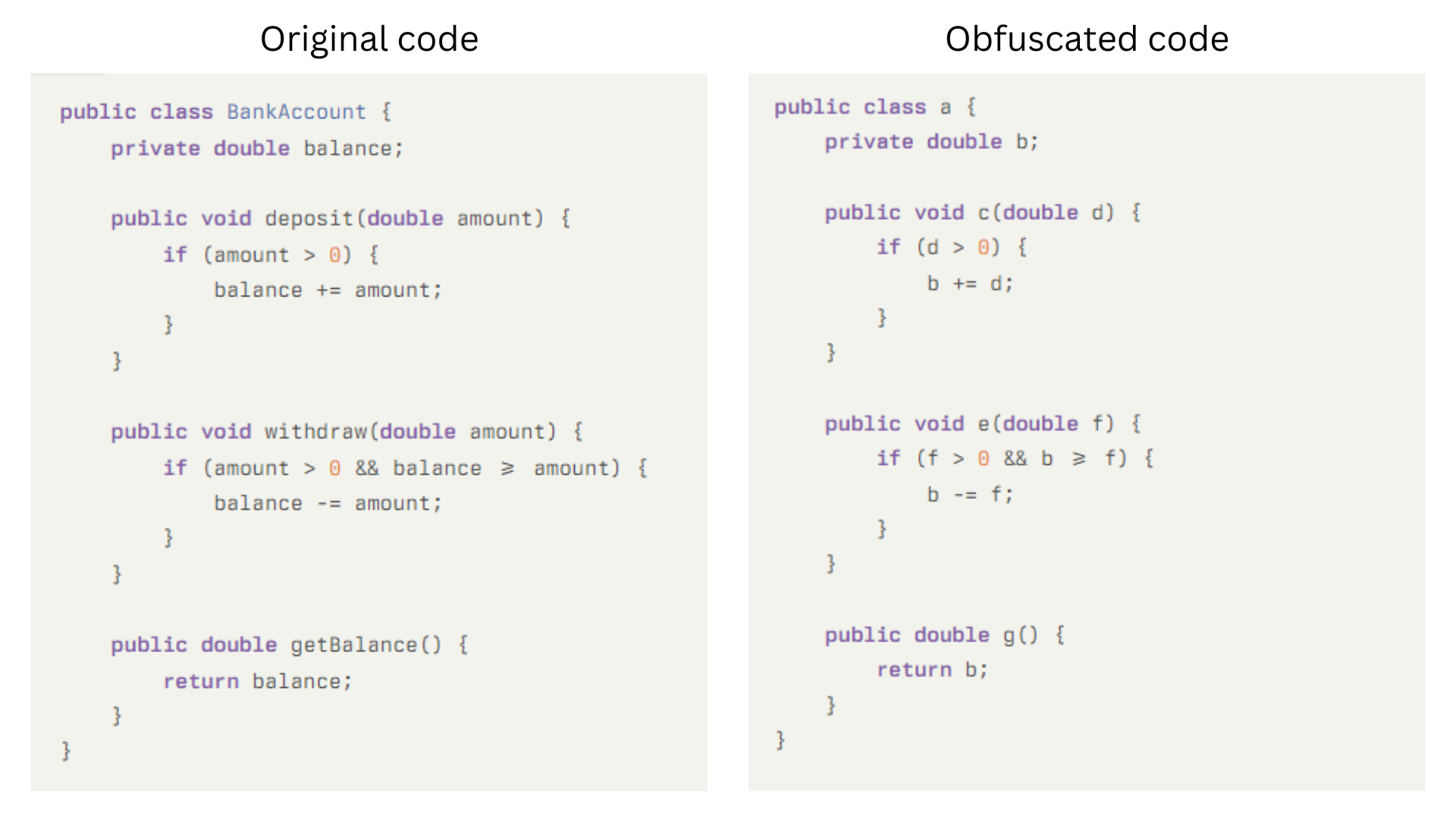
This simplified example demonstrates basic lexical obfuscation while maintaining the code’s functionality.
Best practices for implementing code obfuscation
Use multiple layers
Combine different obfuscation techniques for maximum effectiveness.
Regular updates
Periodically update your obfuscation strategies to stay ahead of evolving reverse engineering techniques.
Balance performance
Ensure that obfuscation doesn’t significantly impact the software’s performance.
Secure the obfuscation process
Protect the tools and processes used for obfuscation to prevent leaks.
How to test if code was properly obfuscated?
Manual code review
Have experienced developers attempt to understand the obfuscated code. This involves carefully analysing the code structure, variable names, and control flow to identify any weaknesses or recognizable patterns that may remain after obfuscation. Manual review is effective for assessing the overall complexity and readability of the obfuscated code.
Best use scenario: Manual code review is most useful when you have a small to medium-sized codebase and want to get a comprehensive understanding of the obfuscation’s effectiveness. It allows for in-depth analysis and the identification of subtle issues that automated tools may miss
Automated tools
Use deobfuscation tools to test the strength of your obfuscation. These tools can help identify common obfuscation patterns, reconstruct the original code structure, and provide insights into the effectiveness of the applied techniques.
Best use scenario: Automated tools are ideal for quickly assessing large codebases or when you need to perform repeated tests. They can provide consistent results and help identify common vulnerabilities or weaknesses in the obfuscation.
Penetration testing
Conduct regular penetration tests to assess the overall security, including the effectiveness of obfuscation. Penetration testing involves simulating real-world attacks to identify vulnerabilities and evaluate the resilience of the obfuscated code. This method can help uncover potential weaknesses that may not be evident through static or dynamic analysis alone.
Best use scenario: Penetration testing is most effective when you want to evaluate the real-world impact of obfuscation and assess its ability to withstand targeted attacks. It is particularly useful for mission-critical applications or those handling sensitive data.
By combining these methods and tailoring them to your specific needs, you can thoroughly test the effectiveness of your code obfuscation and ensure that it provides the desired level of protection against reverse engineering and unauthorized access.
Choosing the right obfuscation tool for your software project
When selecting a code obfuscation tool for your project, consider the following key factors:
Compatibility
Ensure the tool supports your programming language and development environment.
Obfuscation level
Look for a tool that offers the desired level of source code protection, including techniques like name obfuscation, control flow obfuscation, and string encryption.
Performance impact
Evaluate how the obfuscation affects your software’s performance.
Integration
Choose a tool that integrates smoothly with your build process and supports your development workflow.
Version support
Ensure the tool supports the latest versions of your programming language.
Use cases and industry examples
Financial institutions worldwide are increasingly adopting code obfuscation as part of their security strategy. While specific examples are rarely publicized due to security concerns, it’s widely understood in the industry that major banks and investment firms use code obfuscation techniques to protect their high-frequency trading algorithms and other proprietary software. This practice significantly reduces the risk of intellectual property theft and unauthorized access to sensitive financial systems.
However, the consequences of not obfuscating code can be severe. A notable example is the attack on Equifax in 2017. Equifax, one of the largest credit reporting agencies, suffered a massive data breach that exposed the personal information of approximately 147 million people. The attackers exploited a vulnerability in the company’s web application, which was not adequately protected by obfuscation or other security measures. This breach resulted in significant financial losses, legal consequences, and a severe blow to the company’s reputation.
These examples highlight the critical importance of code obfuscation in protecting sensitive information and maintaining the integrity of financial institutions. By implementing robust obfuscation techniques, companies can safeguard their assets and ensure compliance with industry regulations.
How Sollers can help?
Sollers Consulting can assist financial institutions in implementing robust code obfuscation strategies. By leveraging our expertise in software quality assurance and data management, we can help:
- Assess your current code security measures
- Implement appropriate code obfuscation techniques
- Integrate obfuscation into your development lifecycle
- Conduct regular security audits to verify the effectiveness of obfuscation
In conclusion, code obfuscation is not just a technical necessity but a business imperative for financial institutions. By making source code protection a priority, CTOs and development teams can significantly enhance their organization’s security posture, protect valuable intellectual property, and maintain customer trust in an increasingly threat-laden digital landscape.

Kacper Ziatkowski – Consultant at Sollers Consulting, Product Manager of QA tools, member of QA Competence responsible for RFP and RFI
Kacper Ziatkowski is a consultant and Product Manager, specialising in QA and Product Management, where he leads the development of advanced tools such as GoQu and BATS. During his five years with the company, he has coordinated sales processes, actively built QA competence and provided project management support. His focus is on creating business and IT solutions that help insurance companies improve their quality assurance.

Yury Niachayeu – Developer at Sollers Consulting
Yury Niachayeu is a Java developer and information security specialist with a deep passion for sharing his knowledge and expertise. He has honed his programming skills over many years to become an expert in his field. Yury’s wealth of experience and eagerness to learn fuel his passion for coding and sharing insights.
